Bluetooth Mesh Protocol as Applied to Lighting
Little more than one year ago, Bluetooth SIG released the Bluetooth Mesh standardization. Meanwhile, it has become widely adopted and is also one of the favorite systems for lighting controls. Russ Sharer, Vice President of Global Marketing and Business Development for Fulham, starts with an explanation of the Bluetooth Mesh protocol as applied to lighting control and defining its key elements. In a second portion of the article, he answers questions that lighting control evaluators could be asking their vendor.
Every so often, a technology comes along that captures the attention of lighting professionals. Some become widely deployed, others remain just outside mass deployment, and some just die. Lately, using Bluetooth mesh for lighting control has become a muchhyped technology. But why?
Bluetooth mesh offers an open wireless communications standard that is scalable. It's also extensible to provide control and energy management for other systems, which makes LED lighting controls more valuable and the foundation for building automation.
Bluetooth Mesh - The Right Balance of Reliability and Ease of Use
Lighting, after decades of very little modification, is on the cusp of significant change. From the time Edison (or Swan or Davy or whoever) invented the lightbulb, the industry slowly evolved over a century. People's first, and usually, only thought was lighting for illumination. But now lighting has entered the conversation over energy usage and optimization, human and plant health, productivity, and much more. Lighting is also at the center of the largest potential discussion of them all - the interconnection of devices, sensors and machines into an Internet of Things (IoT). Overhyped far ahead of its reality, regardless, IoT is having an impact on how lighting is being connected and controlled, since lighting has emerged as the best endoskeleton for device interconnection. But this communication requires a common language.
Today, lighting controls come in many different options and can do many different things. They can be wired or wireless. They can be a multitude of different protocols, both standardized or proprietary. The inclusion of sensors adds even more value, and creating apps make it all come together. While there are many options available, one option appears to be taking the lead in terms of ease of use, functionality and availability: Bluetooth mesh.
Over the last three years, I have had many conversations with lighting industry professionals, and those discussions explain why Bluetooth mesh will be the most successful technology used for lighting control ever.
What Bluetooth Mesh Makes Different
Bluetooth is a wireless specification developed by Ericsson late in the last century and now controlled by the Bluetooth Special Interest Group (SIG). Everything relating to the Bluetooth mesh standard is now developed by the Bluetooth SIG, in conjunction with its over 33,000 members in 150 countries. The Bluetooth SIG develops the specifications and operates programs to ensure products comply with said specifications. Bluetooth mesh specifies all levels of the communication to ensure an interoperable environment. By the Bluetooth SIG being so forward looking, it has created an ecosystem of various industries, running on the same platform. Nowhere else can you find lighting products, various types of sensors, HVAC devices, building automation devices, etc., using the same technology, allowing the potential of a fully converged, interoperable building. Not to mention that all mobile phones, tablets and PCs this year, will ship with integrated Bluetooth capability, making the system even more prevalent.
Bluetooth was originally specified with a connection structure of Point-to-Point (1:1), then after a few years added Broadcast (1:m). Point-to-point is the most familiar topology, where a single device communicates to another single device, such as a phone sending music to a wireless headset. Yet whatever the connection mechanism, any Bluetooth device can talk to any other.
Bluetooth devices are commonly referred to as nodes once they are provisioned. Provisioning is a secure process that typically involves an application on a handheld, smart device issuing the unprovisioned device a series of security keys that allow it to become part of the Bluetooth network. Once provisioned, nodes have state values that reflect their condition and are shared with the network. This could simply be ON or OFF or a value, such as 50 percent brightness. These state values can be queried by another node or changed through messages.
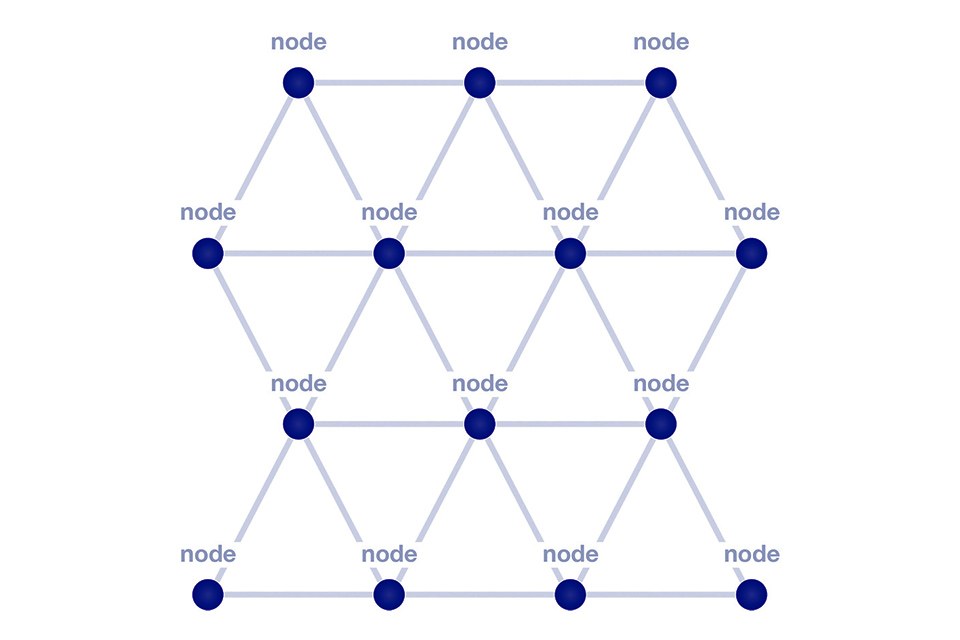
In July 2017, the Bluetooth SIG added the mesh connection structure, giving each node multiple paths to the nodes closest to it (Figure 1). Mesh (m:m) networks allow nodes to have two-way communication between each other, sending and receiving messages throughout the network. Nodes communicate with each other by sending and receiving messages formatted in multiple byte frames (Figure 2). There are two types of messages on a Bluetooth mesh network: access messages and control messages. Application level communication involves access messages. Access messages act upon state values; changing them, retrieving them or delivering them to other nodes in the network. Changing a state value would typically change some physical aspect of the device, like switching it on or off. Control Messages are messages that concern the operation of the Bluetooth mesh network, such as managing relationships of nodes or determining the distance between nodes.
 Figure 2: Basic BT message communication format
Figure 2: Basic BT message communication format
Wireless mesh networks have been around for a while, but Bluetooth mesh is unique and beneficial because it does not need a router or a gateway to collect and distribute commands or data. Instead the network relies on each of the nodes relaying messages from the source node to the destination. Additionally, because messages are transmitted using flooding and are broadcast through multiple nodes, there is no single point of failure; if a single node fails, the messages will simply broadcast to its intended node though different nodes. Flooding means there are generally multiple paths that a message can make it to a node. If a node goes down, the message will still arrive at its destination.
Bluetooth Mesh Networks Are Scalable
Each node in a Bluetooth network is an addressable entity, called an element. Each node has at least one element, the primary element, and may have one or more additional secondary elements (Figure 3). The number and structure of elements does not change throughout the lifetime of a node, as long as it is part of a network, i.e., a switch will always be a switch, a sensor a sensor and a luminaire a luminaire.
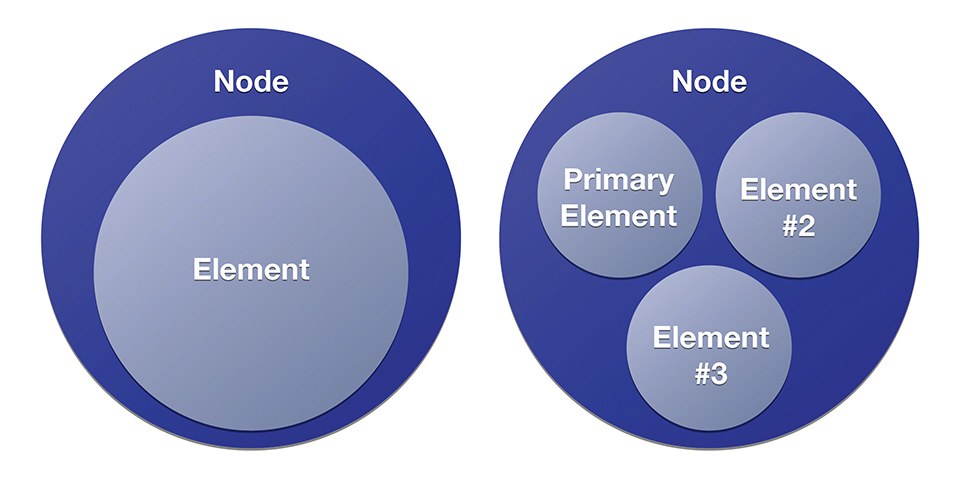 Figure 3: Basic BT node structure - nodes have at least one element, the primary element, and may have one or more additional secondary elements
Figure 3: Basic BT node structure - nodes have at least one element, the primary element, and may have one or more additional secondary elements
Additionally, Bluetooth mesh uses a system of various address types to identify individual elements or sets of elements. There are three primary addresses in a Bluetooth network and a fourth special address type.
Bluetooth network address types:
• Unicast address: uniquely identifies a single element, assigned to
devices during the provisioning process
• Group address: a multicast address that represents one or more
elements. Group addresses are typically used for multiple nodes in a
specific space, such as a room or part of a room
• Virtual address: a way to label a group of like nodes to communicate
mesh messages with the full group with the same virtual address,
regardless of location, instead of addressing specific unique addresses
• Unassigned address: a special address type used to indicate that an
element has not yet been configured or does not have a unicast address
assigned to it
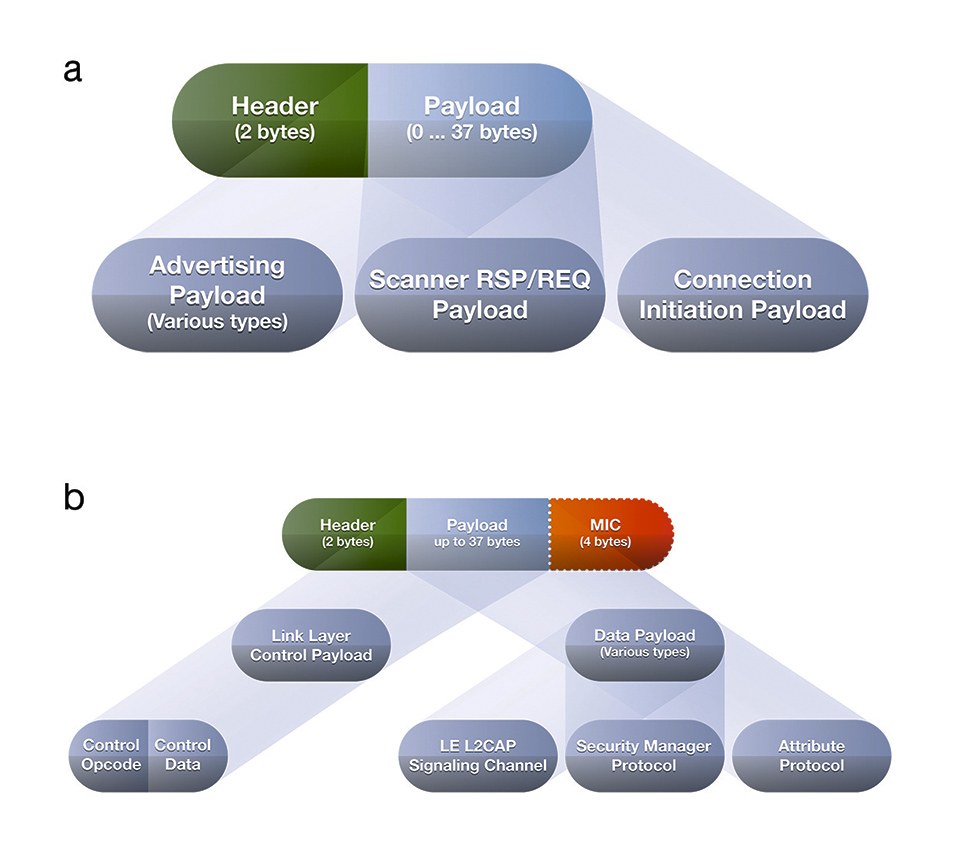 Figure 4: More detailed structure of the BT data transfer structure
Figure 4: More detailed structure of the BT data transfer structure
The primary element is addressed using the first unicast address assigned to the node during provisioning. Each additional secondary element is addressed using the subsequent addresses. These unicast element addresses allow nodes to identify which element within a node is transmitting or receiving a message.
The maximum frame in which a message can be encased is 215 bytes, and when it communicates over Bluetooth 4.2 radio will transmit at 1 megabits per second at distances of up to 60 meters.
The latest Bluetooth 5 spec allows low-energy transmissions to sacrifice data rate for more range, up to four times the range of Bluetooth 4.2 Low Energy, for a maximum of around 100 meters. That's a theoretical maximum, although it's still going to be a huge improvement over older versions of Bluetooth.
Another attribute that varies the transmission distance is the Class of Bluetooth radio. Most of us who have used Bluetooth with our mobile phones realizes that the connection decays and breaks after 4-5 meters. That's because phones and the kinds of devices it attaches to use a Bluetooth Class 1 radio - mostly due to its low power usage. For lighting control, most devices will use a Class 3 radio - extending the transmission distance to over 100 meters.
In addition to the ability to extend range at the expense of bandwidth, Bluetooth 5 adds a new interface to double bandwidth at the expense of power. This new physical layer (PHY) supports speeds of up to 2 megabits per second and higher with transmission power of +20dB in low energy mode.
In other words, the new Bluetooth version offers two interfaces for low energy operation: one to transmit less data over much longer distances, and one to transmit twice the data over a shorter range.
This is great news for devices that need to transmit bursts of large amounts of data (like a firmware update) or for data-hungry applications like audio or video. And, most importantly, Bluetooth 5 is backwards compatible with the older version.
The Bluetooth frame addressing size is 4 bytes. When you do the math, the theoretical maximum number of nodes in a Bluetooth mesh network is 32,767. In real world networks, a network will likely consist of thousands of nodes, and for lighting expect group sizes that more closely align with today's number of lights on an electrical circuit - say 50 to 200. Each circuit can therefore become a sub-network of the overall Bluetooth network.
When considering Bluetooth mesh scalability there are practical limitations for indoor use that can limit the network size. The distance between nodes also is dependent on the material between nodes, such as walls or floors. The more material and the denser the material, the shorter the range becomes. Other variables that will affect distance include the output power of the transmitter, the sensitivity of the receiver and the antennas. In a typical, commercial office trial, no problem could be recognized with nodes communicating with each other through several walls at a distance of 30-40 meters.
SIG-Qualified Bluetooth Mesh Ensures Interoperability
The Bluetooth SIG has published specifications detailing the mesh protocol and specifying each layer of the mesh stack. When vendors implement software in accordance with these standards, their products can be mixed and matched, with the proper security, on any Bluetooth mesh network.
To help ensure compliance and compatibility, the SIG has programs in place to test products to these specifications ensuring interoperability between vendor's products. Note that there are other proprietary Bluetooth products available on the market as well as other wireless mesh protocols available. While these products and protocols may follow part of the SIG specification, they do not necessarily comply totally, so other vendor's Bluetooth devices will not communicate with these proprietary products. Additionally, without following the Bluetooth SIG specification, you compromise the strict reliability, scalability and security expectations that Bluetooth mesh delivers.
It also should be noted that it is possible to adhere to the mesh standard, but still not interoperate with lighting control. To be a totally interoperable node on the mesh requires that the lighting models be implemented as well.
Messages, states and elements are put together with models, which are messages that change the state of a node (Figure 5). Models define and implement the message types, state values and associated behaviors that govern a particular aspect of a node. A node can implement one or more models, and the functionality of any node is determined by the combination of models it implements. While the mesh specification defines lots of different models, there are three basic types of models: client, server and control. Server models contain state, while client models do not; clients only interact with servers by sending and receiving messages. Control Models are a combination of both clients and servers. In all cases, models publish and subscribe to a variety of defined message types, which act upon or report server state values.
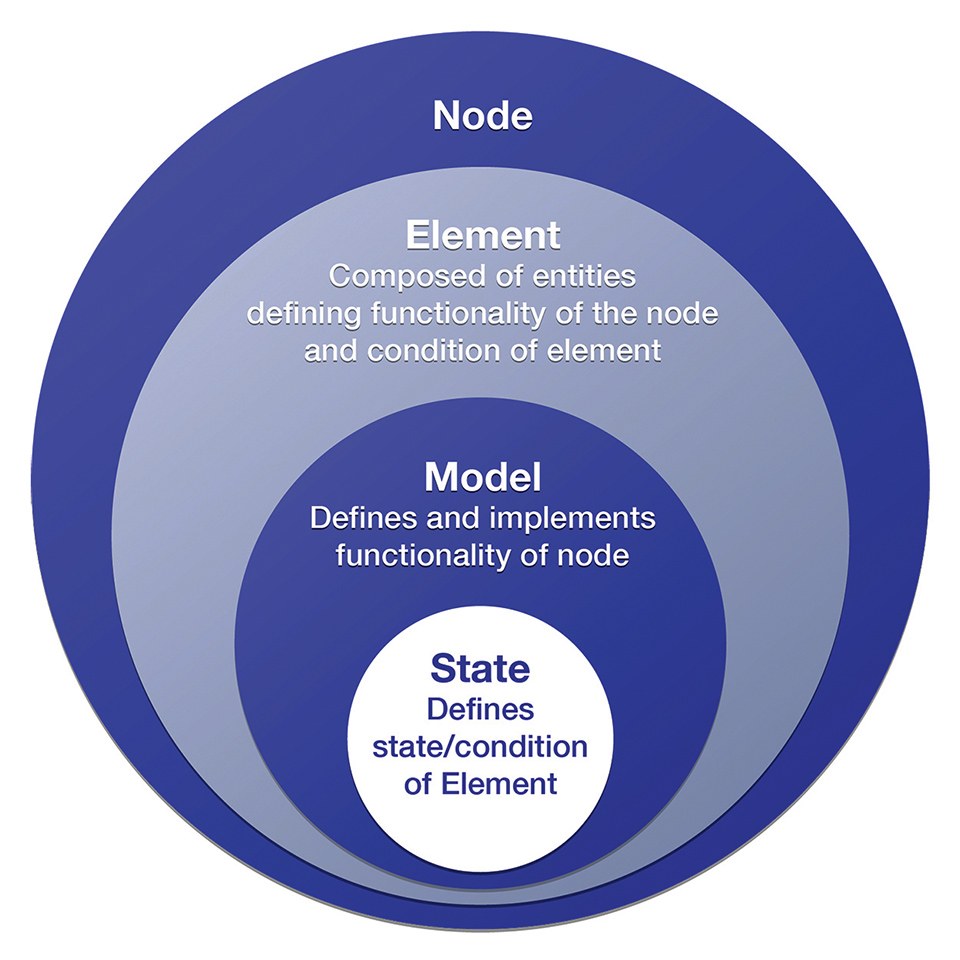 Figure 5: Messages, states and elements are put together with models, which are messages that change the state of a node
Figure 5: Messages, states and elements are put together with models, which are messages that change the state of a node
All Bluetooth SIG-qualified products, including mesh implementations, are listed on the Bluetooth SIG website.
Flooded Mesh Is Efficient and Robust
A flooded mesh or managed flood approach is the easiest way to enable simple, reliable and scalable mesh networks. The managed flood messaging approach of Bluetooth mesh, with its publish/ subscribe group-messaging model, supports extremely efficient messaging for high-performance, large-scale networks.
In a lighting control system, it is important that the correct nodes receive their messages and act accordingly, so Bluetooth uses a publish/subscribe model of communication. Nodes that generate messages publish or send messages, and nodes that receive the messages subscribe or accept messages. At provisioning time, nodes are configured with destination addresses to which they will publish messages or messages to which they will subscribe.
Nodes only respond to messages published from addresses to which they have subscribed, and all others are ignored. When a node publishes a message to a group address, it does not need to know the individual addresses of the nodes that will receive the message. This means that if the set of nodes which have subscribed to that address changes, for example when a new light is added in a particular room, there is no impact at all on the light switch; it will continue to publish ON/OFF messages to all the lights in the assigned group.
In a mesh network, a large percentage of messages will be multicast to group addresses and virtual addresses. If nodes in the same room need to receive a message, the message will not need to look for specific addresses where it needs to send the message; it will flood the message out and the nodes that are assigned to that group will subscribe to the message. A flood approach is the most efficient method for multicast messages.
There are a number of optional characteristics that a node may possess, giving it additional, distinct capabilities within a Bluetooth mesh network. One of these unique characteristics, which is a significant feature of Bluetooth mesh for lighting control, is an energy optimization mechanism called friendship. Some nodes, like sensors, operate using very low energy powered by a small battery that must last for years, or using energy harvesting technology with no batteries. These nodes are referred to as low power nodes or LPN. Other nodes, such as those connected to mains power, have a plentiful supply of power. An LPN will form a partnership with one of the nodes with abundant power; these nodes become friend nodes. A friend node allows an LPN to conserve its limited power by storing a cache of all incoming messages and relaying messages on behalf of the LPN. The friend node stores those messages addressed to the LPN and delivers them when the LPN wakes and requests the messages. Additionally, the friend node delivers security updates to the LPN.
Some people feel that a flooding approach is a waste of bandwidth and creates unnecessary noise because a single message, in theory, could be sent through almost every node in a network. Frequently the argument is heard that the message could continue on forever, hopping from node to node indefinitely. Bluetooth mesh limits the number of hops with a field called TTL (Time to Live); TTL limits the number of hops to no more than 127 hops, although practically, the TTL is set to a significantly smaller number. Bluetooth mesh adds extra intelligence to the system to maximize the efficiency of the hops by requiring all mains-powered nodes to send status updates, called heartbeats, at regular intervals. Heartbeats allow the network to learn its topology, and therefore learns the number of hops to reach each node. This allows each node to set the TTL to the most efficient value. Additionally, every node contains a message cache that looks for duplicate messages to discard to eliminate unnecessary processing further up the network. Bluetooth is optimized for small amounts of data, such as single commands or reports; it is not intended for data-streaming or high-bandwidth applications.
For applications such as lighting control, flooded mesh is easier and more efficient to deploy and manage than routed mesh. Routed networks are much more complicated because each node needs to be assigned a function, such as a routing node, central hub or coordinator. Then a routing table and algorithms are used to tell messages which path, or which nodes, a message should take. This creates a chance for significant network interruptions and creates potential for a single point of failure. It also increases the cost of each node in the system.
Bluetooth Mesh Is Designed To Be Secure
Bluetooth mesh was designed with security as its highest priority. First, security in Bluetooth mesh is mandatory. Nodes, the network and individual applications cannot be compromised in any way because of a multitude of fundamental security measures. Bluetooth is concerned with more than just securing individual nodes or connections between nodes, it is concerned with securing the entire network.
Security with Bluetooth mesh starts with the nodes but doesn't end there. Nodes are provisioned using 256-bit elliptic curves and out-of-the-box authentication. Messages also are secured using AES CCM authentication and encryption with 128-bit keys; each message has a minimum of 64 bits of authentication, with the possibility to have up to 1088 bits of authentication for the longest messages. Not only are all messages encrypted and authenticated, but encryption and authentication also take place at the network and application layers.
To further enhance authentication and encryption, Bluetooth mesh separates network security, application security and device security, addressing each independently using application keys, device keys and network keys. Additionally, these security keys can be changed during the life of the mesh network via a key refresh procedure. There also is isolation in Bluetooth mesh networks so they can be divided into subnets, each cryptographically distinct and secure from the others.
All of these Bluetooth mesh features prevent any kind of security attack that is currently known to man. Brute-force attacks are prevented by using 128-bit keys with a minimum of 64-bit authentication on every message. Replay attacks are stopped by using a new sequence of numbers on every message sent and checking those on every message received. Man-in-the-middle attacks are avoided using ECDH cryptography during provisioning with out-of-band authentication. Trashcan attacks are prevented using a key-refresh procedure, allowing keys in all remaining devices and blacklisting the removed/broken devices; in other words, should someone disassemble a thrown-out device it can't reveal any security information. Physically insecure device attacks are eliminated by permitting devices in an insecure location to have separate keys to those in a secure location; for example, this stops someone from accessing a Bluetooth luminaire and sending a message to unlock a door. Visitor attacks are prevented by giving guests and visitors temporary and limited access to the network using a separate set of keys; these guest keys have a limited lifetime. Also, Bluetooth mesh uses a message obfuscation procedure. Since there are no identifying values, such as the source or destination address, an attacker cannot know where a message was sent, thus protecting the user's identity. Each time a message is relayed, this obfuscated information is changed, removing the ability to track message flow.
Why Bluetooth Mesh Is the Preferred Wireless Addressing Standard
There are wireless alternatives to Bluetooth mesh. Zigbee, for example, is a mature wireless competitor for lighting control with a variety of products available on the market today. While there are some benefits to the use of ZigBee, there are concerns that have prevented its wider adoption, including system cost, security and reliability. First, a Zigbee network is dependent on a gateway to form and administer the wireless network. The theoretical maximum number of notes per network is 240; anything with more nodes will need another gateway and will have to be treated as a separate network. Speed is a concern in Zigbee, which can transmit ~250 kb/sec versus 1,000 kb/sec with Bluetooth mesh. The maximum node limitations and the slower speed greatly limits the scalability of Zigbee in large projects, especially if the network controls more than just lights. Furthermore, Zigbee does not specify the full stack, so there are interoperability issues. In other words, not all Zigbee products can easily communicate with each other.
Thread is another wireless mesh network protocol based on IPv6. Like Zigbee, Thread does not specify the full stack (in Bluetooth terminology models) so there is little interoperability between vendor's applications. At provisioning time, Thread takes a two-step approach: one step to set up network and a second step to add logic, such as creating rules and zones; with Bluetooth, all of this takes place in a single step. Thread also needs a gateway or hub for the devices to communicate. All of this limits the scalability of a Thread network.
Taken together, along with the fact that the use of Bluetooth in so many consumer products makes the cost of silicon very low, Bluetooth mesh clearly offers a simple to use, scalable, interoperable and robust low-power communications structure on which to build lighting control systems. Unlike any other wireless technology, including Wi-Fi which has significantly higher power usage levels, Bluetooth and its mesh communications topology and lighting models will deliver the promise of lighting control at a reasonable price point, which can be extended for other IoT applications.